
How Static and Hybrid Analysis Can Cut Privacy Review Effort by 95%
22 Jan 2026
An automated approach to identifying and categorizing personal data processing in source code, reducing privacy reviews to just 4.2% of methods.

What 100 GitHub Projects Reveal About Personal Data in Modern Software
22 Jan 2026
A large-scale analysis of 100 open-source apps shows how focused privacy code reviews can efficiently identify personal data and PII handling.
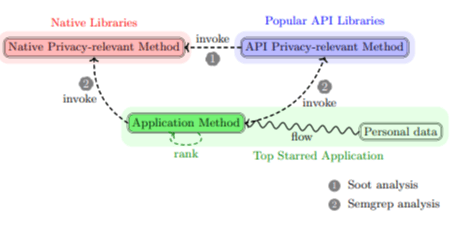
Data-Driven Ranking Reveals Where Privacy Risks Actually Live in Java and JavaScript Code
22 Jan 2026
A data-driven study ranks privacy-relevant methods in Java and JavaScript, showing developers where personal data truly flows in real codebases.
How Static Analysis Can Expose Personal Data Hidden in Source Code
21 Jan 2026
A practical overview of how static analysis and pattern matching can identify personal data and PII hidden inside Java and JavaScript codebases.
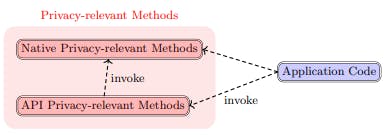
Tracing Personal Data Through APIs
21 Jan 2026
Learn how to identify privacy-relevant API methods using dependency analysis and GDPR-aligned labels to improve software privacy reviews.
Automating Privacy Code Reviews by Mapping How Software Handles Personal Data
21 Jan 2026
An overview of how privacy-relevant methods can improve automated code reviews by identifying and categorizing personal data processing under GDPR.

Reducing Privacy Code Review Overhead With Privacy-Relevant Methods
21 Jan 2026
An automated static analysis approach that identifies privacy-relevant methods, reducing privacy code reviews to under 5% of a codebase.

How Bias, Context, and Data Gaps Shape What We Know About Code Security
19 Jan 2026
An in-depth look at internal, construct, and external validity threats when studying software security issues through code review data.

Why Your Code Review Process Might Be Missing Its Biggest Security Risks
19 Jan 2026
Code reviews flag coding weaknesses far more often than vulnerabilities—revealing gaps, risks, and how teams can improve secure review practices.